2 PCI Signal Descriptions
2.1 System Pins
CLK
Clock provides the timing reference for all transfers on the PCI bus. All PCI signals except reset and interrupts are sampled on the rising edge of the CLK signal. All bus timing specifications are defined relative to the rising edge. For most PCI systems the CLK signal operates at a maximum frequency of 33 MHz. To operate at 66MHz, both the PCI system and the PCI add-in board must be specifically designed to support the higher CLK frequency. A 66 MHz system will supply a 66 MHz CLK if the add-in board supports it, and supply a default 33 MHz CLK if the add-in board does not support the higher frequency. Likewise, if a system is capable of providing only a 33 MHz clock, then a 66 MHz add-in board must be able to operate using the lower frequency. The minimum frequency of the CLK signal is specified at 0 Hz permitting CLK to be “suspended” for power saving purposes.
 RST#
RST#
Reset is driven active low to cause a hardware reset of a PCI device. The reset shall cause a PCI device’s configuration registers, state machines, and output signals to be placed in their initial state. RST# is asserted and deasserted asynchronously to the CLK signal. It will remain active for at least 100 microseconds after CLK becomes stable.
2.2 Address and Data Pins
AD[31:0]
Address and Data are multiplexed onto these pins. AD[31:0] transfers a 32-bit physical address during “address phases”, and transfers 32-bits of data information during “data phases”. An address phase occurs during the clock following a high to low transition on the FRAME# signal. A data phase occurs when both IRDY# and TRDY# are asserted low. During write transactions the initiator drives valid data on AD[31:0] during each cycle it drives IRDY# low. The target drives TRDY# low when it is able to accept the write data. When both IRDY# and TRDY# are low, the target captures the write data and the transaction is completed. For read transactions the opposite occurs. The target drives TRDY# low when valid data is driven on AD[31:0], and the initiator drives IRDY# low when it is able to accept the data. When both IRDY# and TRDY# are low, the initiator captures the data and the transaction is completed. Bit 31 is the most significant AD bit. Bit 0 is the least significant AD bit.
C/BE[3:0]#
Bus Command and Byte Enables are multiplexed onto these pins. During the address phase of a transaction these signals carry the bus command that defines the type of transfer to be performed. During the data phase of a transaction these signals carry byte enable information. C/BE[3]# is the byte enable for the most significant byte (AD[31:24]) and C/BE[0]# is the byte enable for the lease significant byte (AD[7:0]). The C/BE[3:0]# signals are driven only by the initiator and are actively driven through the all address and data phases of a transaction.
PAR
Parity is even parity over the AD[31:0] and C/BE[3:0]# signals. Even parity implies that there is an even number of ’1′s on the AD[31:0], C/BE[3:0]#, and PAR signals. The PAR signal has the same timings as the AD[31:0] signals, but is delayed by one cycle to allow more time to calculate valid parity.
2.3 Interface Control Pins
FRAME#
Cycle Frame is driven low by the initiator to signal the start of a new bus transaction. The address phase occurs during the first clock cycle after a high to low transition on the FRAME# signal. If the initiator intends to perform a transaction with only a single data phase, then it will return FRAME# back high after only one cycle. If multiple data phases are to be performed, the initiator will hold FRAME# low in all but the last data phase. The initiator signals its intent to perform a master initiated termination by driving FRAME# high during the last data phase of a transaction. During a target initiated termination the initiator will continue to drive FRAME# low through the end of the transaction.
IRDY#
Initiator Ready is driven low by the initiator as an indication it is ready to complete the current data phase of the transaction. During writes it indicates the initiator has placed valid data on AD[31:0]. During reads it indicates the initiator is ready to accept data on AD[31:0]. Once asserted, the initiator holds IRDY# low until TRDY# is driven low to complete the transfer, or the target uses the STOP# signal to terminate without performing the data transfer. IRDY# permits the initiator to insert wait states as needed to slow the data transfer.
TRDY#
Target Ready is driven low by the target as an indication it is read to complete the current data phase of the transaction. During writes it indicates the target is ready to accept data on AD[31:0]. During reads it indicates the target has placed valid data on the AD[31:0] signals. Once asserted, the target holds TRDY# low until IRDY# is driven low to complete the transfer. TRDY# permits the target to insert wait states as needed to slow the data transfer.
STOP#
Stop is driven low by the target to request the initiator terminate the current transaction. In the event that a target requires a long period of time to respond to a transaction, it may use the STOP# signal to suspend the transaction so the bus can be used to perform other transfers in the interim. When the target terminates a transaction without performing any data phases it is called a retry. If one or more data phases are completed before the target terminates the transaction, it is called a disconnect. A retry or disconnect signals the initiator that it must return at a later time to attempt performing the transaction again. In the event of a fatal error such as a hardware problem the target may use STOP# and DEVSEL# to signal an abnormal termination of the bus transfer called a target abort. The initiator can use the target abort to signal system software that a fatal error has been detected.
LOCK#
Lock may be asserted by an initiator to request exclusive access for performing multiple transactions with a target. It prevents other initiators from modifying the locked addresses until the agent initiating the lock can complete its transaction. Only specific regions (a minimum of 16 bytes) of the target’s addresses are locked for exclusive access. While LOCK# is asserted, other non-exclusive transactions may proceed with addresses that are not currently locked. But any non-exclusive accesses to the target’s locked address space will be denied via a retry operation. LOCK# is intended for use by bridge devices to prevent deadlocks.
IDSEL
Initialization Device Select is used as a chip select during PCI configuration read and write transactions. IDSEL is driven by the PCI system and is unique on a per slot basis. This allows the PCI configuration mechanism to individually address each PCI device in the system. A PCI device is selected by a configuration cycle only if IDSEL is high, AD[1:0] are “00″ (indicating a type 0 configuration cycle), and the command placed on the C/BE[3:0]# signals during the address phase is either a “configuration read” or “configuration write”. AD[10:8] may be used to select one of up to eight “functions” within the PCI device. AD[7:2] select individual configuration registers within a device and function.
DEVSEL#
Device Select is driven active low by a PCI target when it detects its address on the PCI bus. DEVSEL# may be driven one, two, or three clocks following the address phase. DEVSEL# must be asserted with or prior to the clock edge in which the TRDY# signal is asserted. Once DEVSEL# has been asserted, it cannot be deasserted until the last data phase has completed, or the target issues a target abort. If the initiator never receives an active DEVSEL# it terminates the transaction in what is termed a master abort.
2.4 Arbitration Pins (Initiator Only)
REQ#
Request is used by a PCI device to request use of the bus. Each PCI device has its own unique REQ# signal. The arbiter in the PCI system receives the REQ# signals from each device. It is important that this signal be tri-stated while RST# is asserted to prevent a system hang. This signal is implemented only be devices capable of being an initiator.
GNT#
Grant indicates that a PCI device’s request to use the bus has been granted. Each PCI device has its own unique GNT# signal from the PCI system arbiter. If a device’s GNT# signal is active during one clock cycle, then the device may begin a transaction in the following clock cycle by asserting the FRAME# signal. This signal is implemented only be devices capable of being an initiator.
2.5 Error Reporting Pins
PERR#
Parity Error is used for reporting data parity errors during all PCI transactions except a “Special Cycle”. PERR# is driven low two clock periods after the data phase with bad parity. It is driven low for a minimum of one clock period. PERR# is shared among all PCI devices and is driven with a tri-state driver. A pull-up resistor ensures the signal is sustained in an inactive state when no device is driving it. After being asserted low, PERR# must be driven high one clock before being tri-stated to restore the signal to its inactive state. This ensures the signal does not remain low in the following cycle because of a slow rise due to the pull-up.
SERR#
System Error is for reporting address parity errors, data parity errors during a Special Cycle, or any other fatal system error. SERR# is shared among all PCI devices and is driven only as an open drain signal (it is driven low or tri-stated by PCI devices, but never driven high). It is activated synchronously to CLK, but when released will float high asynchronously through a pull-up resistor.
2.6 Interrupt Pins
INTA#, INTB#, INTC#, INTD#
Interrupts are driven low by PCI devices to request attention from their device driver software. They are defined as “level sensitive” and are driven low as an open drain signal. Once asserted, the INTx# signals will continue to be asserted by the PCI device until the device driver software clears the pending request. A PCI device that contains only a single function shall use only INTA#. Multi-function devices (such as a combination LAN/modem add-in board) may use multiple INTx# lines. A single function device uses INTA#. A two function device uses INTA# and INTB#, etc. All PCI device drivers must be capable of sharing an interrupt level by chaining with other devices using the interrupt vector.
2.1 System Pins
CLK
Clock provides the timing reference for all transfers on the PCI bus. All PCI signals except reset and interrupts are sampled on the rising edge of the CLK signal. All bus timing specifications are defined relative to the rising edge. For most PCI systems the CLK signal operates at a maximum frequency of 33 MHz. To operate at 66MHz, both the PCI system and the PCI add-in board must be specifically designed to support the higher CLK frequency. A 66 MHz system will supply a 66 MHz CLK if the add-in board supports it, and supply a default 33 MHz CLK if the add-in board does not support the higher frequency. Likewise, if a system is capable of providing only a 33 MHz clock, then a 66 MHz add-in board must be able to operate using the lower frequency. The minimum frequency of the CLK signal is specified at 0 Hz permitting CLK to be “suspended” for power saving purposes.
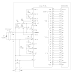
Figure 1: Signals defined in the PCI standard.
Reset is driven active low to cause a hardware reset of a PCI device. The reset shall cause a PCI device’s configuration registers, state machines, and output signals to be placed in their initial state. RST# is asserted and deasserted asynchronously to the CLK signal. It will remain active for at least 100 microseconds after CLK becomes stable.
2.2 Address and Data Pins
AD[31:0]
Address and Data are multiplexed onto these pins. AD[31:0] transfers a 32-bit physical address during “address phases”, and transfers 32-bits of data information during “data phases”. An address phase occurs during the clock following a high to low transition on the FRAME# signal. A data phase occurs when both IRDY# and TRDY# are asserted low. During write transactions the initiator drives valid data on AD[31:0] during each cycle it drives IRDY# low. The target drives TRDY# low when it is able to accept the write data. When both IRDY# and TRDY# are low, the target captures the write data and the transaction is completed. For read transactions the opposite occurs. The target drives TRDY# low when valid data is driven on AD[31:0], and the initiator drives IRDY# low when it is able to accept the data. When both IRDY# and TRDY# are low, the initiator captures the data and the transaction is completed. Bit 31 is the most significant AD bit. Bit 0 is the least significant AD bit.
C/BE[3:0]#
Bus Command and Byte Enables are multiplexed onto these pins. During the address phase of a transaction these signals carry the bus command that defines the type of transfer to be performed. During the data phase of a transaction these signals carry byte enable information. C/BE[3]# is the byte enable for the most significant byte (AD[31:24]) and C/BE[0]# is the byte enable for the lease significant byte (AD[7:0]). The C/BE[3:0]# signals are driven only by the initiator and are actively driven through the all address and data phases of a transaction.
PAR
Parity is even parity over the AD[31:0] and C/BE[3:0]# signals. Even parity implies that there is an even number of ’1′s on the AD[31:0], C/BE[3:0]#, and PAR signals. The PAR signal has the same timings as the AD[31:0] signals, but is delayed by one cycle to allow more time to calculate valid parity.
2.3 Interface Control Pins
FRAME#
Cycle Frame is driven low by the initiator to signal the start of a new bus transaction. The address phase occurs during the first clock cycle after a high to low transition on the FRAME# signal. If the initiator intends to perform a transaction with only a single data phase, then it will return FRAME# back high after only one cycle. If multiple data phases are to be performed, the initiator will hold FRAME# low in all but the last data phase. The initiator signals its intent to perform a master initiated termination by driving FRAME# high during the last data phase of a transaction. During a target initiated termination the initiator will continue to drive FRAME# low through the end of the transaction.
IRDY#
Initiator Ready is driven low by the initiator as an indication it is ready to complete the current data phase of the transaction. During writes it indicates the initiator has placed valid data on AD[31:0]. During reads it indicates the initiator is ready to accept data on AD[31:0]. Once asserted, the initiator holds IRDY# low until TRDY# is driven low to complete the transfer, or the target uses the STOP# signal to terminate without performing the data transfer. IRDY# permits the initiator to insert wait states as needed to slow the data transfer.
TRDY#
Target Ready is driven low by the target as an indication it is read to complete the current data phase of the transaction. During writes it indicates the target is ready to accept data on AD[31:0]. During reads it indicates the target has placed valid data on the AD[31:0] signals. Once asserted, the target holds TRDY# low until IRDY# is driven low to complete the transfer. TRDY# permits the target to insert wait states as needed to slow the data transfer.
STOP#
Stop is driven low by the target to request the initiator terminate the current transaction. In the event that a target requires a long period of time to respond to a transaction, it may use the STOP# signal to suspend the transaction so the bus can be used to perform other transfers in the interim. When the target terminates a transaction without performing any data phases it is called a retry. If one or more data phases are completed before the target terminates the transaction, it is called a disconnect. A retry or disconnect signals the initiator that it must return at a later time to attempt performing the transaction again. In the event of a fatal error such as a hardware problem the target may use STOP# and DEVSEL# to signal an abnormal termination of the bus transfer called a target abort. The initiator can use the target abort to signal system software that a fatal error has been detected.
LOCK#
Lock may be asserted by an initiator to request exclusive access for performing multiple transactions with a target. It prevents other initiators from modifying the locked addresses until the agent initiating the lock can complete its transaction. Only specific regions (a minimum of 16 bytes) of the target’s addresses are locked for exclusive access. While LOCK# is asserted, other non-exclusive transactions may proceed with addresses that are not currently locked. But any non-exclusive accesses to the target’s locked address space will be denied via a retry operation. LOCK# is intended for use by bridge devices to prevent deadlocks.
IDSEL
Initialization Device Select is used as a chip select during PCI configuration read and write transactions. IDSEL is driven by the PCI system and is unique on a per slot basis. This allows the PCI configuration mechanism to individually address each PCI device in the system. A PCI device is selected by a configuration cycle only if IDSEL is high, AD[1:0] are “00″ (indicating a type 0 configuration cycle), and the command placed on the C/BE[3:0]# signals during the address phase is either a “configuration read” or “configuration write”. AD[10:8] may be used to select one of up to eight “functions” within the PCI device. AD[7:2] select individual configuration registers within a device and function.
DEVSEL#
Device Select is driven active low by a PCI target when it detects its address on the PCI bus. DEVSEL# may be driven one, two, or three clocks following the address phase. DEVSEL# must be asserted with or prior to the clock edge in which the TRDY# signal is asserted. Once DEVSEL# has been asserted, it cannot be deasserted until the last data phase has completed, or the target issues a target abort. If the initiator never receives an active DEVSEL# it terminates the transaction in what is termed a master abort.
2.4 Arbitration Pins (Initiator Only)
REQ#
Request is used by a PCI device to request use of the bus. Each PCI device has its own unique REQ# signal. The arbiter in the PCI system receives the REQ# signals from each device. It is important that this signal be tri-stated while RST# is asserted to prevent a system hang. This signal is implemented only be devices capable of being an initiator.
GNT#
Grant indicates that a PCI device’s request to use the bus has been granted. Each PCI device has its own unique GNT# signal from the PCI system arbiter. If a device’s GNT# signal is active during one clock cycle, then the device may begin a transaction in the following clock cycle by asserting the FRAME# signal. This signal is implemented only be devices capable of being an initiator.
2.5 Error Reporting Pins
PERR#
Parity Error is used for reporting data parity errors during all PCI transactions except a “Special Cycle”. PERR# is driven low two clock periods after the data phase with bad parity. It is driven low for a minimum of one clock period. PERR# is shared among all PCI devices and is driven with a tri-state driver. A pull-up resistor ensures the signal is sustained in an inactive state when no device is driving it. After being asserted low, PERR# must be driven high one clock before being tri-stated to restore the signal to its inactive state. This ensures the signal does not remain low in the following cycle because of a slow rise due to the pull-up.
SERR#
System Error is for reporting address parity errors, data parity errors during a Special Cycle, or any other fatal system error. SERR# is shared among all PCI devices and is driven only as an open drain signal (it is driven low or tri-stated by PCI devices, but never driven high). It is activated synchronously to CLK, but when released will float high asynchronously through a pull-up resistor.
2.6 Interrupt Pins
INTA#, INTB#, INTC#, INTD#
Interrupts are driven low by PCI devices to request attention from their device driver software. They are defined as “level sensitive” and are driven low as an open drain signal. Once asserted, the INTx# signals will continue to be asserted by the PCI device until the device driver software clears the pending request. A PCI device that contains only a single function shall use only INTA#. Multi-function devices (such as a combination LAN/modem add-in board) may use multiple INTx# lines. A single function device uses INTA#. A two function device uses INTA# and INTB#, etc. All PCI device drivers must be capable of sharing an interrupt level by chaining with other devices using the interrupt vector.