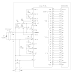
3. PCI Bus Transactions
Bus commands indicate to the target the type of transaction the master is requesting. Bus commands are encoded on the C/BE[3:0]# lines during the address phase. PCI bus command encodings and types are listed below, followed by a brief description of each.
The I/O Read command is used to read data from an agent mapped in I/O Address space. AD[31::00] provide a byte address. All 32 bits must be decoded. The byte enables indicate the size of the transfer and must be consistent with the byte address.
The I/O Write command is used to write data to an agent mapped in I/O Address space. All 32 bits must be decoded. The byte enables indicate the size of the transfer and must be consistent with the byte address.
Reserved commands encoding are reserved for future use. PCI targets must not alias reserved commands with other commands. Target must not respond to reserved encoding. If a reserved encoding is used on the interface, the access typically will be terminated with Master-Abort.
The Memory read command is used to read the data from an agent mapped in the Memory Address Space. The target is free to do an anticipatory read for this command only if it can guarantee that such a read will have no side effects. Furthermore, the target must ensure the coherency (which includes ordering) of any data retained in temporary buffers after this PCI transaction is completed. Such buffers must be invalidated before any synchronization events (e.g. updating an I/O status register or memory flag) are passed through this access path.
The Memory Write command is used to write data to an agent mapped in Memory Address Space. When the target returns “ready,” it has assumed responsibility for the coherency (which includes ordering) of the subject data. This can be done either by implementing this command in a fully synchronous manner, or by insuring any software transparent posting buffer will be flushed before synchronization events (e.g. updating an I/O status register or memory flag) are passed through this access path. This implies that the master is free to create a synchronization event immediately after using this command.
The Configuration Read command is used to read the Configuration Space of each agent. An agent is selected during a configuration access when its IDSEL signal asserted and AD[1::0] are 00. During the address phase of a configuration transaction, AD[7::2] address one of the 64 DWORD registers ( where byte enables address the byte(s) Within each DWORD) in Configuration Space of each device and AD[31::11] or logical don’t cares to the selected agent. AD[10::08] indicate which device of a multi-function agent is being addressed.
The Configuration Write command is used to transfer data to the configuration Space of each agent. Addressing for configuration write transaction is the same for configuration read transactions.
The Memory Read Multiple command semantically identical to the memory Read command except that it additionally indicates that master may intend to fetch more than one cacheline before disconnecting. The memory controller continues pipelining memory requests as long as FRAME# is asserted. This command is intended to be used with bulk sequential data transfer where the memory system (and the requesting master) might gain some performance advantage by sequentially reading ahead one or more additional cacheline(s) when a software transparent buffer is available for temporary storage.
The Dual Address Cycle (DAC) command is used to transfer a 64- bit address to devices that supports the 64-bit addressing when the address is not in the low 4-GB address space. Targets that support only 32 bit address must treat this command as reserved and not respond to the current transaction in any way.
The Memory read line command is semantically identically to the Memory read command except that it additionally indicates that the master intends to fetch a complete cacheline. This command is intended to be used with bulk sequential data transfers where the memory system (and the requesting) might gain some performance advantage by reading up to cacheline boundary in response to the request rather than a single memory cycle. As with the memory read command, pre-fetch buffers must be invalidated before any synchronization events are passed through this access path.
The Memory write and invalidate command is semantically identical to memory write command except that it additionally graduates a minimum transfer of one complete cacheline i.e. the master intend to write all bytes within the addressed cacheline in a single PCI transaction unless interrupted by the target. Note: All byte enables must be asserted during each data phase for this command. The master may allow the transaction to cross a cacheline boundary only if it intends to transfer the entire next line also. This command requires implementation of a configuration register in the master indicating the cacheline size and may only be used with linear burst ordering. It allows a memory performance optimization by invalidation a dirty line in a write-back cache without requiring the actual write-back cycle thus shortening access time.
Bus commands indicate to the target the type of transaction the master is requesting. Bus commands are encoded on the C/BE[3:0]# lines during the address phase. PCI bus command encodings and types are listed below, followed by a brief description of each.
| C/BE[3:0]# | Command Types |
| 0000 | Interrupt Acknowledge |
| 0001 | Special Cycle |
| 0010 | I/O Read |
| 0011 | I/O Write |
| 0100 | Reserved |
| 0101 | Reserved |
| 0110 | Memory Read |
| 0111 | Memory Write |
| 1000 | Reserved |
| 1001 | Reserved |
| 1010 | Configuration Read |
| 1011 | Configuration Write |
| 1100 | Memory Read Multiple |
| 1101 | Dual Address Cycle |
| 1110 | Memory Read Line |
| 1111 | Memory Write and Invalidate |
The I/O Write command is used to write data to an agent mapped in I/O Address space. All 32 bits must be decoded. The byte enables indicate the size of the transfer and must be consistent with the byte address.
Reserved commands encoding are reserved for future use. PCI targets must not alias reserved commands with other commands. Target must not respond to reserved encoding. If a reserved encoding is used on the interface, the access typically will be terminated with Master-Abort.
The Memory read command is used to read the data from an agent mapped in the Memory Address Space. The target is free to do an anticipatory read for this command only if it can guarantee that such a read will have no side effects. Furthermore, the target must ensure the coherency (which includes ordering) of any data retained in temporary buffers after this PCI transaction is completed. Such buffers must be invalidated before any synchronization events (e.g. updating an I/O status register or memory flag) are passed through this access path.
The Memory Write command is used to write data to an agent mapped in Memory Address Space. When the target returns “ready,” it has assumed responsibility for the coherency (which includes ordering) of the subject data. This can be done either by implementing this command in a fully synchronous manner, or by insuring any software transparent posting buffer will be flushed before synchronization events (e.g. updating an I/O status register or memory flag) are passed through this access path. This implies that the master is free to create a synchronization event immediately after using this command.
The Configuration Read command is used to read the Configuration Space of each agent. An agent is selected during a configuration access when its IDSEL signal asserted and AD[1::0] are 00. During the address phase of a configuration transaction, AD[7::2] address one of the 64 DWORD registers ( where byte enables address the byte(s) Within each DWORD) in Configuration Space of each device and AD[31::11] or logical don’t cares to the selected agent. AD[10::08] indicate which device of a multi-function agent is being addressed.
The Configuration Write command is used to transfer data to the configuration Space of each agent. Addressing for configuration write transaction is the same for configuration read transactions.
The Memory Read Multiple command semantically identical to the memory Read command except that it additionally indicates that master may intend to fetch more than one cacheline before disconnecting. The memory controller continues pipelining memory requests as long as FRAME# is asserted. This command is intended to be used with bulk sequential data transfer where the memory system (and the requesting master) might gain some performance advantage by sequentially reading ahead one or more additional cacheline(s) when a software transparent buffer is available for temporary storage.
The Dual Address Cycle (DAC) command is used to transfer a 64- bit address to devices that supports the 64-bit addressing when the address is not in the low 4-GB address space. Targets that support only 32 bit address must treat this command as reserved and not respond to the current transaction in any way.
The Memory read line command is semantically identically to the Memory read command except that it additionally indicates that the master intends to fetch a complete cacheline. This command is intended to be used with bulk sequential data transfers where the memory system (and the requesting) might gain some performance advantage by reading up to cacheline boundary in response to the request rather than a single memory cycle. As with the memory read command, pre-fetch buffers must be invalidated before any synchronization events are passed through this access path.
The Memory write and invalidate command is semantically identical to memory write command except that it additionally graduates a minimum transfer of one complete cacheline i.e. the master intend to write all bytes within the addressed cacheline in a single PCI transaction unless interrupted by the target. Note: All byte enables must be asserted during each data phase for this command. The master may allow the transaction to cross a cacheline boundary only if it intends to transfer the entire next line also. This command requires implementation of a configuration register in the master indicating the cacheline size and may only be used with linear burst ordering. It allows a memory performance optimization by invalidation a dirty line in a write-back cache without requiring the actual write-back cycle thus shortening access time.